What is Zero Trust?
What is Zero Trust?
Core Principles of Zero Trust
At C-STEM, we understand that securing your organisation’s digital assets is more critical than ever. The Zero Trust framework is a modern cyber security approach that emphasises “never trust, always verify.” This means that all users, whether inside or outside your organisation, must be authenticated, authorised, and continuously validated for security configuration and posture before accessing applications or data.
Zero Trust begins with identity verification, ensuring that only authorised individuals, devices, and processes can access your resources. It then assesses the security compliance of device endpoints, including IoT systems on the edge.
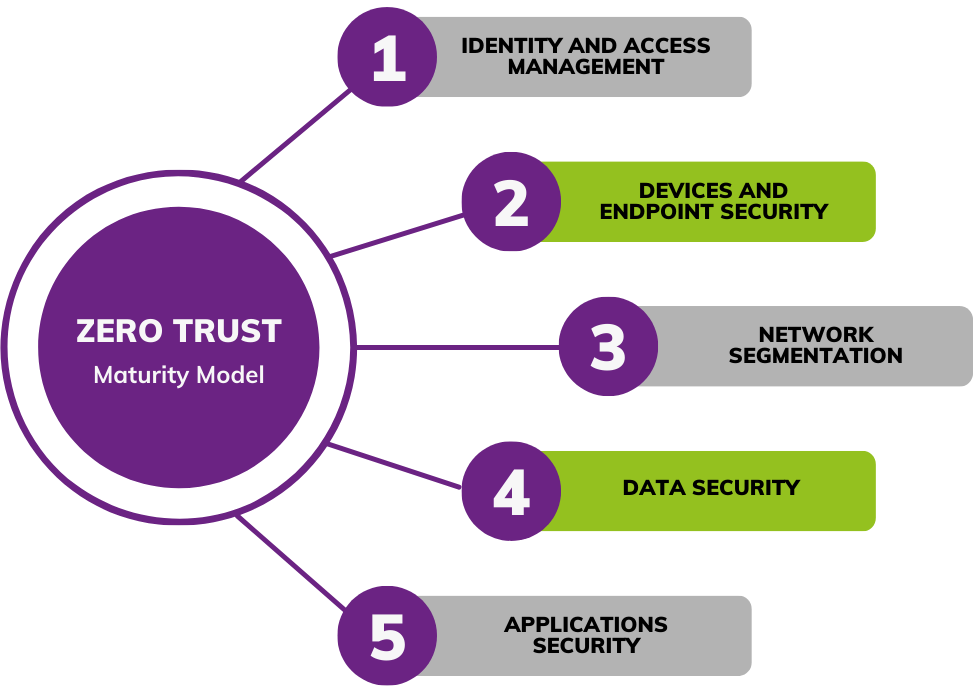
Why Zero Trust?
Organisations today are more focused on security than ever before, aiming to protect customer trust, enhance workforce mobility, and unlock new digital business opportunities. Zero Trust is the modern answer to ensuring optimal security and availability of systems and data. By implementing a Zero Trust Architecture (ZTA), organisations move beyond traditional network controls, integrating identity, device behaviour, and context to make more granular, intelligent, and adaptive access decisions.
Critical Business Outcomes
Adopting a Zero Trust model involves careful planning and decision-making, from engaging stakeholders to evaluating risks and technologies, and managing organisational change. C-STEM, as a ZTA MSP, engages to support the more efficient delivery and maintenance of the following 7 ZT critical business outcomes, via the qualified introduction of the appropriate elements of our evolved ZTA SMART Solutions.
- Improved security posture – Minimise security risks and protect cloud infrastructure and data.
- Seamless cloud adoption – Securely transition to the cloud with strong foundational security practices.
- Compliance and regulatory alignment – Meet industry standards like CE, CE+, DORA, DSPT, CAF, NIS2, HIPAA, and PCI DSS.
- Enhanced data protection – Implement robust encryption, access controls, and regular security assessments.
- Efficient incident response – Detect and respond to security events swiftly and effectively.
- Improved workforce productivity – Support flexible work environments while maintaining security.
- Enable digital transformation – Securely interconnect devices, facilities, and processes beyond traditional network perimeters.
Systems + Techniques = Effective Management
C-STEM - Platfform Building, 11-20 Devon Place, Newport NP20 4NW
Tel: 0345 241 0000 | Fax: 0345 241 0001
C-STEM is the trading name for Communication-STEM Limited. Registered Office: 10 Temple Back, Bristol, BS1 6FL. Registered in England 03270429. VAT no. 682398492












